Cyberattacks are getting smarter, faster, and more damaging—relying on even the best antivirus software for business isn’t enough anymore.
Modern threats like ransomware, zero-day exploits, and social engineering attacks can easily bypass basic defenses on both computers and mobile devices. Even the most trusted antivirus tools often fail to catch what’s really out there and keep your business safe.
That’s why today’s businesses need a more innovative strategy: layered, proactive cybersecurity built to adapt.
In this article, we’ll break down where traditional antivirus falls short, what a strong defense actually looks like, and how to build a modern security stack that genuinely keeps your business safe.
Cyber Threats Today: It’s More Than Just Viruses Now
Gone are the days when a sketchy email with a bad attachment was your biggest worry. Cyber threats have grown up: they’ve gotten more sophisticated, sneakier, and much more expensive.
Modern Cyber Threats
Today’s cyberattacks are more like precision strikes than random spam blasts. Let’s break down a few of the big ones:
- Ransomware locks up your data and demands payment to get it back. And yes, it’s as bad as it sounds.
- Phishing attacks trick people into handing over credentials or sensitive info, usually by pretending to be someone they trust.
- Zero-day exploits target software vulnerabilities that developers don’t even know exist yet. No patch, no protection against malware or other threats.
- APTs (Advanced Persistent Threats) are like digital spies. They quietly sneak in, stay hidden, and steal sensitive data over time—often without you noticing for months.
These aren’t one-off attacks. They’re calculated, persistent, and built to cause severe damage.
Statistics on Evolving Threats
If it feels like cyberattacks are getting worse, that’s because they are.
IBM’s 2024 Cost of a Data Breach report says the global average financial losses from a breach hit $4.88 million in 2024—a 15% jump in just three years. And it’s not just big companies getting hit. Small and medium-sized businesses are equally vulnerable.
Verizon’s 2024 Data Breach Investigations Report reveals that 74% of breaches involved a human element, like phishing or stolen credentials. Translation: attackers aren’t just going after your systems, they’re going after people.
Real-World Examples of Advanced Attacks
Let’s talk about what this looks like in the real world.
Remember Stuxnet? Back in 2007, this ultra-sophisticated worm targeted Iran’s nuclear facilities. It was a veritable digital weapon, showing the world how vulnerable industrial control systems really are, especially for private-sector business owners.
Then there was NotPetya in 2017. What started as a fake ransomware attack quickly spread across global networks, crippling companies and causing billions in damage. It’s still considered one of the most destructive cyberattacks in history, and an example of why protection against malware is a must for any business.
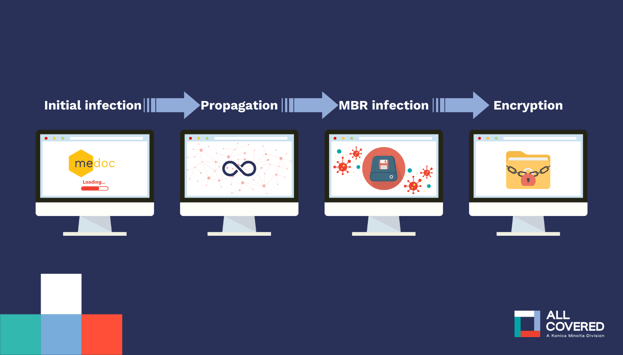
Bottom line? Cyber threats today are strategic, expensive, and evolving fast.
Vulnerabilities Exposed: What Basic Antivirus Programs Miss
Here’s the thing: cybercriminals aren’t taking time off. The FBI and CISA recently warned that a fresh wave of ransomware attacks is targeting businesses of all sizes. It’s fast, coordinated, and brutal. If you think your old-school antivirus has you covered, it might be time for a reality check.
Unpatched Software and Zero-Day Exploits
One of the easiest ways hackers get in? Outdated software. If a vulnerability hasn’t been patched, it’s an open door—and basic antivirus won’t stop someone from walking through it.
Even worse are zero-day exploits, which take advantage of flaws no one knows about yet. Traditional antivirus tools rely on known threats. Zero-days are, by definition, unknown. They can’t offer protection against malware that they don’t know exists.
Human Error and Social Engineering
The most significant risk in your company might not be your network. It might be your people.
People make mistakes. Someone clicks a sketchy link, shares a password, or downloads something they shouldn’t. Phishing emails, fake logins, shady links—social engineering plays on human instinct, not tech weaknesses. And no, your antivirus doesn’t know your office manager just clicked on a “free Amazon gift card” link.
The Inadequacy of Reactive Security
Old-school antivirus tools are reactive: they wait for a threat to appear, then try to stop it. But by the time that happens, the damage could already be done. Modern online threats need real-time scanning and proactive defense, not a software program that performs automatic updates once a day and crosses its fingers.
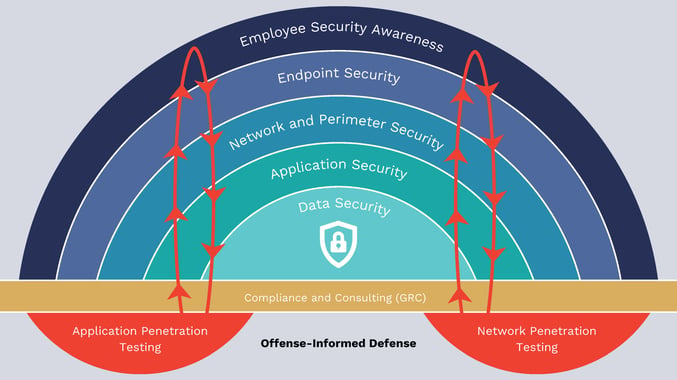
Proactive Security: Real-Time Monitoring, Threat Intelligence & Offense-Informed Defense
Cybersecurity isn’t just about locking the doors—it’s about watching the windows, checking the cameras, and constantly asking: What’s the next move an attacker might make? Prevention is critical, but it's never enough without ongoing monitoring and real-world testing.
Real-Time Monitoring & Threat Intelligence
Security Information and Event Management (SIEM) tools are the backbone of real-time visibility. They collect telemetry across your network, like logins, file changes, and network traffic, and flag suspicious patterns as they emerge.
But having alerts isn’t enough. Online threats evolve too fast. That’s where threat intelligence comes in. It connects the dots between what’s happening in your environment and what’s happening in the wider world—new ransomware variants, emerging vulnerabilities, and shifting attack patterns.
At All Covered, SIEM isn’t siloed. It’s integrated into a broader ecosystem of security services. That means faster response times, fewer blind spots, and a clearer picture of what’s happening across your organization.
Offense-Informed Defense: What Makes All Covered Different
Here’s where things really stand out: Most companies keep offense and defense separate. They might outsource pen testing once a year and call it good. But the people defending your systems rarely talk to the ones trying to break into them.
All Covered flips that model. Our red team (offense) and blue team (defense) work side by side, under one roof. Penetration testing isn’t a one-off report—it’s a constant feedback loop.
This approach—Offense-Informed Defense—means real-world attack simulations shape your security strategy. We find the gaps before attackers do, and our defensive playbook evolves accordingly.
Recommended Implementation Order
Here’s a practical path to stronger security, especially for SMBs or mid-sized enterprises just starting to level up:
- Security Awareness Training: Start with your people. Reduce human error from day one.
- Managed EDR: Get eyes on your endpoints with real-time protection.
- Multi-Factor Authentication (MFA): Easy win, colossal impact.
- Incident Response Planning: Know what to do when something happens.
- M365 Manage and Protect: Lock down your Microsoft environment.
- SIEM: Bring it all together with visibility and correlation.
The All Covered Solution: A Strategic Cybersecurity Partnership
Basic business antivirus solutions alone can’t withstand today’s complex cyber threats and keep your business safe. As ransomware, social engineering, and zero-day exploits continue to evolve, businesses need more than just reactive tools—they need a comprehensive, proactive defense strategy.
That’s where All Covered comes in. We don’t offer one-size-fits-all solutions—we build tailored cybersecurity strategies that align with your business goals, infrastructure, and risk profile. With integrated services like Managed EDR, SIEM, real-time threat intelligence, and in-house penetration testing, we help organizations stay one step ahead of attackers.
From prevention to advanced threat detection to response, All Covered is your trusted partner in cybersecurity resilience.
Ready to strengthen your defenses? Explore All Covered’s Cybersecurity Services, or download our NIST Cybersecurity Framework Checklist.



